1.Using Comand Promt
firstly , open Ragnarok Online, login and choose the
after that run command prompt
| command prompt or DOS terminal windows. Start -> Run -> "cmd" Win9x Start -> Run -> "command" |
after that, u need to type netstat , press enter and u will see ragnarok online ip address .
2.Using WPE
1. Download WPE and extract it.
3. At WPE's window, click on Target Programs button.
4. A window will open, search for the server's executable and double-click it.
6. Switch to your Ragnarok's window, put and try to login.
8. A window will open with recorded data. One of the packets sent to the server would be login packet which usually contains the server's version, master_version, IP and port - write them down because they are going to be used later. The packets will be different on each server, possible login packets may start with 64 00 or 02 B0. Other packets (such as 18-byte-long 02 04) may be sent before login packet.
2. Open your ragnarok but don't login yet! Leave it on the login screen and open Wireshark.
3. At Wireshark's window, go to Capture > Options on the upper menu or press Ctrl + K.
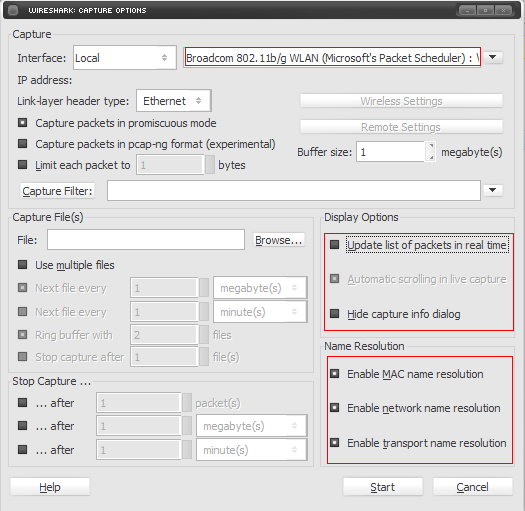
4. In the top right box, select the interface that will be used to capture on. If there isn't any specific interface to use, select the one whose IP address is equal to the your ip address or is not unknown. Alternatively you can try all of them and use the one that records the packets. Set the others settings like the images bellow:
5. Click on Start button and go back to the Ragnarok window and login.
7. In Wireshark main window, you can see the TCP segments that were captured. Fill in the packet filter, but what to fill in depends on the username you used to login.
10. A new window will open, in the bottom left, select Hex Dump.
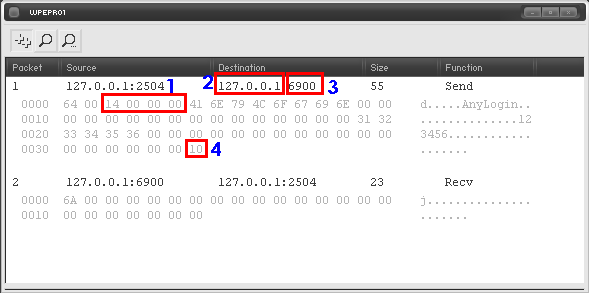
11. These are the login packets. Take a look at it and write down the packets that contains the version and master version numbers. They are marked on the image bellow.
Converting can be made using Windows' calculator or any other site that has a hex to dec calculator.
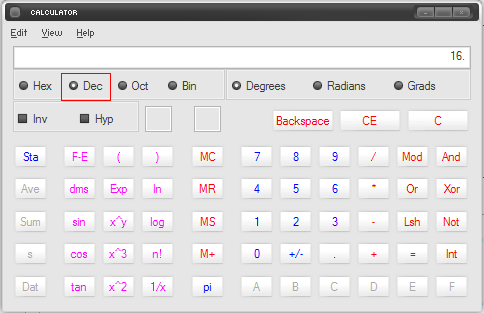
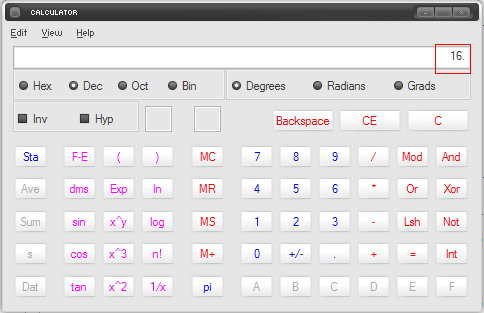
1. Open Windows calculator Start > Accessories > Calculator.
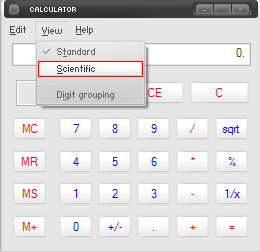
2. Go to View on the upper menu and click on Scientific.
3. Check the circle beside Hex.
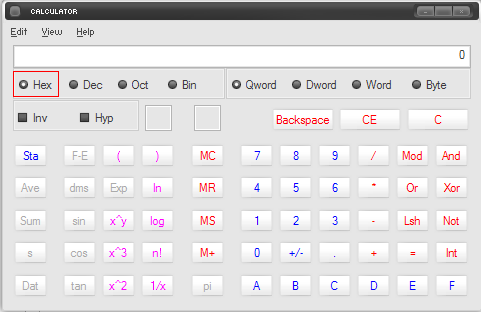
4. On the calculator, type the number that you got for master_version and version. In the example, master_version hexadecimal number is 10.
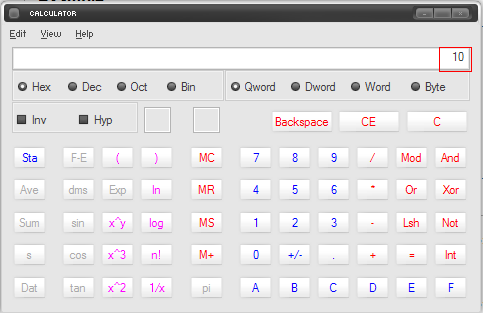
5. Check the circle beside Dec.
6. After checking, the number shown should automatically be converted from hexadecimal to decimal.
If your server is not listed in the file, then add a new entry. If your server is already listed, then modify the existing entry.
3. At WPE's window, click on Target Programs button.
4. A window will open, search for the server's executable and double-click it.
- Note. Some servers "hide" their executables by renaming it (like from xxxRO.exe to xxxx.dll or xxxxx.bin), so don't worry if the executable isn't a .exe one.
6. Switch to your Ragnarok's window, put and try to login.
- Note. Valid login information are not needed.
8. A window will open with recorded data. One of the packets sent to the server would be login packet which usually contains the server's version, master_version, IP and port - write them down because they are going to be used later. The packets will be different on each server, possible login packets may start with 64 00 or 02 B0. Other packets (such as 18-byte-long 02 04) may be sent before login packet.
- Legend:
- version (displayed as 4-byte unsigned number in little-endian, in hex)
- IP (as is)
- port (as is)
- master version (displayed as 1-byte unsigned number, in hex)
Wireshark
1. Download and install Wireshark.2. Open your ragnarok but don't login yet! Leave it on the login screen and open Wireshark.
3. At Wireshark's window, go to Capture > Options on the upper menu or press Ctrl + K.
4. In the top right box, select the interface that will be used to capture on. If there isn't any specific interface to use, select the one whose IP address is equal to the your ip address or is not unknown. Alternatively you can try all of them and use the one that records the packets. Set the others settings like the images bellow:
5. Click on Start button and go back to the Ragnarok window and login.
- Note. Valid information are not needed.
7. In Wireshark main window, you can see the TCP segments that were captured. Fill in the packet filter, but what to fill in depends on the username you used to login.
- Enter this in the "Filter" text box:
eth contains "xxxxxx" or eth contains xxxxxx
- Replace xxxxxx with the username that was used to login and press enter. In the example bellow, username was Mushroom.
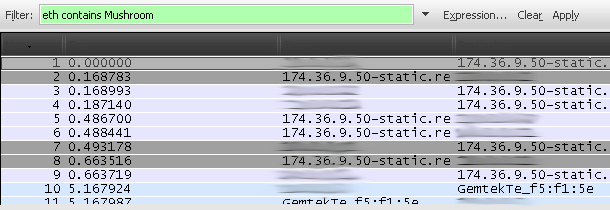
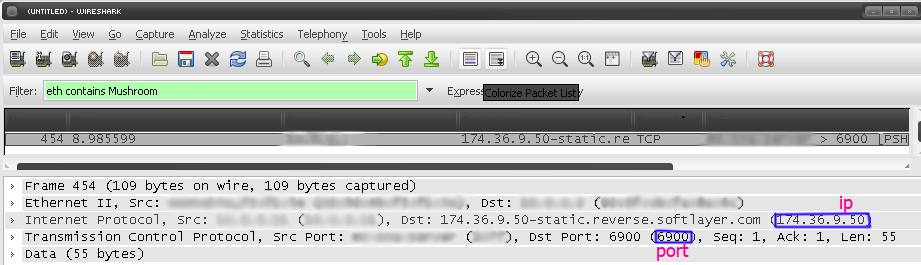
- Write down the IP and port.
10. A new window will open, in the bottom left, select Hex Dump.
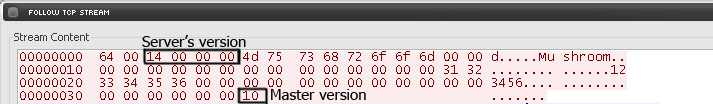
11. These are the login packets. Take a look at it and write down the packets that contains the version and master version numbers. They are marked on the image bellow.
- version displayed as 4-byte unsigned number in little-endian, in hex
- master version displayed as 1-byte unsigned number, in hex
Converting Hexadecimal to Decimal numbers
Master_version and server version collected from the login packets are in hexadecimal number (base-16) and Kore expects a decimal number (base-10), so converting those numbers are needed before Kore can read them.Converting can be made using Windows' calculator or any other site that has a hex to dec calculator.
1. Open Windows calculator Start > Accessories > Calculator.
2. Go to View on the upper menu and click on Scientific.
3. Check the circle beside Hex.
4. On the calculator, type the number that you got for master_version and version. In the example, master_version hexadecimal number is 10.
5. Check the circle beside Dec.
6. After checking, the number shown should automatically be converted from hexadecimal to decimal.
- You must convert master_version and version.
Configuring Openkore
OpenKore reads server information from a file named servers.txt. The file is on tables folder.If your server is not listed in the file, then add a new entry. If your server is already listed, then modify the existing entry.
Syntax
[<server name>] ip <number/host> port <number> version <number> master_version <number> serverType <serverType name> serverEncoding <enconding> charBlockSize <number> addTableFolders <folder path> #Following configs are optional captcha <boolean flag> chatLangCode <boolean flag> field_<location> <filename> clientHash <hex string> gameGuard <number> private <boolean flag> paddedPackets <boolean flag> paddedPackets_attackID <packet switches> paddedPackets_skillUseID <packet switches> secureLogin <boolean flag> secureLogin_type <type> secureLogin_requestCode <hex string> secureLogin_account <boolean flag> storageEncryptKey <encrypt key> recvpackets <file name> masterLogin_packet <packet switch>
Required
- [<server name>]
- The name of the server that you want to bot. The name must be between [ ].
- ip <number/host>
- Server's login IP.
- port <number>
- Server's login port number.
- version <number>
- Server's version (converted from hex to decimal).
- master_version <number>
- Server's master_version (converted from hex to decimal).
| The following documentation describes a feature that was greatly changed in SVN trunk (latest development version) since the last release. It may work differently or not be available if you're using 2.0.7 or any older version. |
- Server's type. Each official server has its own serverType, private servers must use kRO serverTypes according to executables dates.
- serverEncoding
- Characters encoding type. The character encoding cannot be automatically detected, but here's a list of possible character encodings that you can use:
Encoding Language used Western Language which uses a Roman-based alphabet. Example: English, German, French, Portuguese, Indonesian, etc. Simplified Chinese Simplified Chinese. Traditional Chinese Traditional Chinese. Korean Korean Russian Russian, or a Cyrillic-based language. Japanese Japanese Thai Thai
- charBlockSize <value>
- Character block (inner structure for character list packet) size. May be 106 (default), 108, 112, 116; with renewal servers, 128, 132 and 136. Correct value for a server may be not supported by a specific serverType or not supported at all, so merely trying values mentioned here may not be enough.
| Implementation of this feature is expected to become outdated with server updates. As OpenKore is a free project, if you stumble upon such updates, you are expected to fix the problem and contribute your changes back. Usually, server supporters will do that, but there isn't any for random private servers, and some official ones may not always be covered. |
- addTableFolders <folder path>
- Configures Kore to load tables file from the specified path (relative to the tables directory).
- Used only when there is no --tables specified.
- For english ones, you can use
addTableFolders translated/kRO_english
- or
addTableFolders iRO
Optional
- captcha <boolean flag>
- Configure Kore to use the captcha 'protocol'.
- chatLangCode <boolean flag>
- gameGuard <number>
- Used for GameGuard and HackShield. See also: Poseidon.
- private <boolean flag>
- Set this option if Openkore connects to a wrong map-server IP. Usually for private servers.
- recvpackets <file name.txt>
- Configures file's name for recvpackets. See also: Packet Length Extractor.
- masterLogin_packet <packet switch>
- Overrides master login packet switch (but not its structure). Required for XKore 2 if it's different from 0064.
Example
[MushroomRO] ip 127.0.0.1 port 6900 master_version 16 version 20 serverType kRO_RagexeRE_2010_01_26a charBlockSize 108 serverEncoding Western recvpackets mush-recvpackets.txt addTableFolders iRO


No comments:
Post a Comment